Compliance
Overview
The compliance tool performs comprehensive compliance checks on PR code changes, validating them against security standards, ticket requirements, and custom organizational compliance checklists, thereby helping teams, enterprises, and agents maintain consistent code quality and security practices while ensuring that development work aligns with business requirements.


Example Usage
Manual Triggering
Invoke the tool manually by commenting /compliance on any PR. The compliance results are presented in a comprehensive table:
To edit configurations related to the compliance tool, use the following template:
For example, you can enable ticket compliance labels by running:
Automatic Triggering
The tool can be triggered automatically every time a new PR is opened, or in a push event to an existing PR.
To run the compliance tool automatically when a PR is opened, define the following in the configuration file:
Compliance Categories
The compliance tool evaluates three main categories:
1. Security Compliance
Scans for security vulnerabilities and potential exploits in the PR code changes:
Verified Security Concerns 🔴: Clear security vulnerabilities that require immediate attention
Possible Security Risks ⚪: Potential security issues that need human verification
No Security Concerns 🟢: No security vulnerabilities detected
Examples of security issues:
Exposure of sensitive information (API keys, passwords, secrets)
SQL injection vulnerabilities
Cross-site scripting (XSS) risks
Cross-site request forgery (CSRF) vulnerabilities
Insecure data handling patterns
2. Ticket Compliance
How to set up ticket compliance
Auto-create ticket
Follow this guide to learn how to enable triggering create tickets based on PR content.
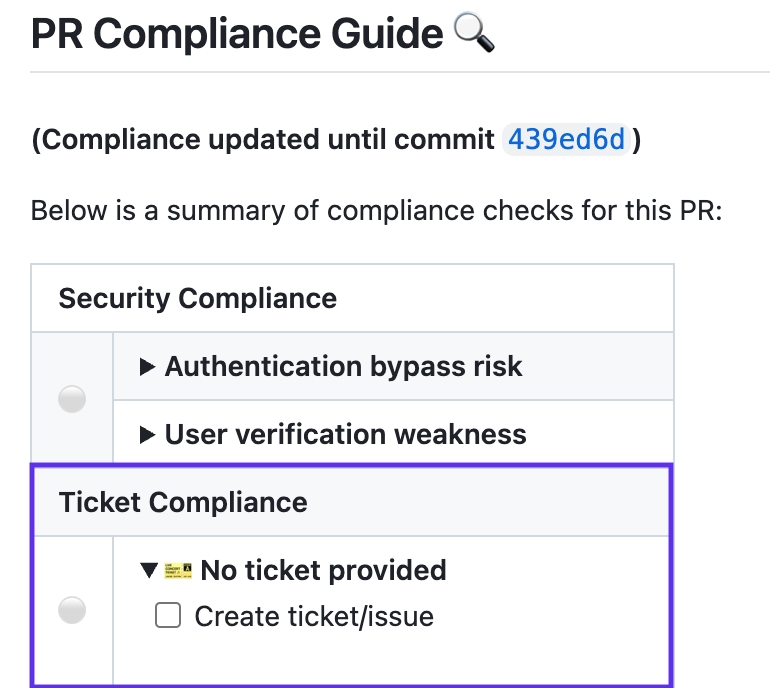
Validates that PR changes fulfill the requirements specified in linked tickets:
Fully Compliant 🟢: All ticket requirements are satisfied
Partially Compliant 🟡: Some requirements are met, others need attention
Not Compliant 🔴: Clear violations of ticket requirements
Requires Verification ⚪: Requirements that need human review
3. RAG Code Duplication Compliance
Analyzes code changes using RAG endpoint to detect potential code duplication from the codebase:
Fully Compliant 🟢: No code duplication found
Not Compliant 🔴: Full code duplication found
Requires Verification ⚪: Near code duplication
Validates against an organization-specific compliance checklist:
Fully Compliant 🟢: All custom compliance are satisfied
Not Compliant 🔴: Violations of custom compliance
Requires Verification ⚪: Compliance that need human assessment
Last updated